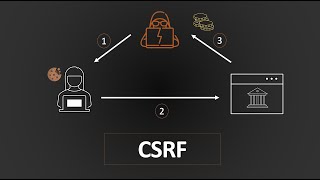
Cross-Site Request Forgery (CSRF) Explained
Vložit
- čas přidán 31. 05. 2024
- #WebSecurity #CSRF
A video explaining CSRF and some different types of attacks.
🔗 CSRF to RCE : github.com/zadam/trilium/issu...
SPONSORED BY INTIGRITI - intigriti.com
Sorry for the late upload, was busy with other stuff.
🎵 Track: Warriyo - Mortals (feat. Laura Brehm)
NCS link: • Warriyo - Mortals (fea...








Seriously cant say it enough. I freaking love your videos
I second that notion
@4:53
one of the important things to mention here is that the csrf token is good only as long as it is mapped to the user's session ID in the backend. Otherwise, the attacker might simply obtain a valid CSRF token by visiting the main website themself and inject it into the malicious requests.
Tying the token to the user's session and validating that on the backend for each request is very important.
There's tens of thousands of videos on Csrf but you easily beat all of them. Yet the number of views you got aren't nearly as close as theirs. Niche youtubers like you are ahead of the time. I hope people like you are revered in coming 5 years
Yeah, late in the game, but it's totally fine, I'm just trying to give somethin back to the community.
Look at it now ;)
Damn, dude really planted the seed and let it grow
"Cat-Site Request Forgery"
Man, I tried researching how CSRF attacks worked last year and I never got a solid grasp of it.
This video changed that.
As a cybersecurity enthusiast and web developer, this is super helpful!
i came from LiveOverflow channel , i so glad to be here !
your channel is interesting , love it . keep up the good work
No words to describe how much informational these videos are.
Thank you.
Incredibly amazing video as always. Very great explanation, and I love your color choices and how you draw/write everything
Just came by from watching LiveOverflow's video. I subbed and put on the bell notification on. This channel looks so cool
You put lots of effort into your videos. Transitions are amazing. Wonderful production.
Came from Stök's channel. Absolutely loving it now! Subscribed and belled👏
I often find it hard to focus on educational videos like this, but somehow your videos have all of my attention. Not sure what voodoo you're using but it's working!
You are just awesome man. Why doesn't CZcams show such search results at the top. I couldn't find you when I needed but now I am happy. Thanks bro..
Wow , I love the graphical explanatory video, really easy to follow and understand in concordance with explication
Amazing content as always, big fan of your videos and tutorials, thank you so much ;D
was curious if tokens really work since you could just make a GET and read the token then post. glad you answered that question very quickly. awesome video. i will subscribe
Third video of yours that came up, and perfectly described the concept. Subscribed
we need more of these.
literally a free service to everyone genuinely interested
I really enjoyed your theme of explanation and the background music. sounded adventurous
the music and naration in the intro made me feel like I'm discovering a mistery in another new world, lol. great video
This is one of the best channel I have encountered 😍
Great video, to the point and thoroughly explained the main concept.
you concept and style of teaching is lovely!..keep it up
This is very well explained, appreciated
You definitely deserve more subs ;)
Love the style of explanation!
Videos are so interesting and clear with basic to advance. Keep going 😀
Great Video and your drawing is amazing bro that google logo and the adobe logo was so perfect.
Great content. I can't believe this is free!
PS: I love your colour scheme
Bruh you need to create more content like this. Also you give example are to fast but over all your the best. 11/10.
Great explanation bro, Keep up the good work.
Wish ya da best.
Wunderbar...................U r one awsme teacher. Hats off to the effort you put in, for us mere novices.
Thankyou for your videos. I would very much like to see a video on Insecure CORS and ways to escalate it :)
I genuinely don't understand why you stop creating videos. Your style is so cool.
He's back!
You need more likes. Your work is needed for every developer.
Such a good video. I love the voice as well: cute and reliable
Crystal clear explanation. Thanks a ton
Awesome video. I hope that you explain some bugs like vulnerable flash files, JSONP and email spoofing
As I understand it, fetch and XHR require `useCredentials` to send the cookies along with the request which needs to be explicitly stated on the CORS header Access-Control-Allow-Credentials. Otherwise cookies are not being sent and the CSRF fails.
Amazing video, so clear!
thank you
I watched around 15 videos regarding csrf and you are the only one who explained it clearly. Also not everyone stressed on "the browser automatically sends the cookies".
truuu
I still don't understand it. What does it mean? What cookies? All the cookies from all the tabs opened in the browser are sent with all POST requests that are being made on whichever tab?
@@kornelijekovac9793 All the cookies from one website will be sent to the server of that website on each request (with website I mean domain, not origin). The most important cookie is the one with the session id (SID), which identifies the user. More about this can be found if you search for "session management".
@@bsmldy8681 But how can cookies from two different tabs intermingle?
not sure what you mean by that
Thanks for making this. Really nice!
Very clear explanation. Thanks!
the best channel, thanks brother for the knowledge
your channel is a gold mine !!
Thank you for the great explanation! How did you made that animated slides, what tool is it?
Best explanation I've ever heard!
Well done sir, keep them coming! :)
Explained well, props to you
Was watching live overflows vid a month ago, and look at me now, watching each video of yours everyday
As someone who pioneered csrf in 2007 this is a great video
Great videos.........Thank you for posting them
probably the best explanation out there
That's crazy explanation, Thanks a lot
Love your videos! Please make more :3
Just amazing content!
Awesome explanation! Tks!
Amazing 😅 , i learn a lot of new concepts in one video , but i think i will re-watch it later , some of them seem confusing !
I love your videos there amazing , professional ! but I guess slow down a little bit for new people,
other than that your the best I have ever being taught
Do you buy the domains for the video? Is do you have some sort of local domain stuff
love your videos this is a god's work
Excellent Explanation
this made me rethink my web security holy shit.
Great Explanation ✅
You explained this better than the skillsoft guys, that's for sure
Thank you very much!
Awesome ! Thank you !
This is awesome !
Which software do you use for animation?
you should make more cyber security videos i LOVE them!!!
You're videos are awesome
since im new to this and just learning.. let me see if i got this straight. in order for me to make this work all i have to do is write a js file using the code here, host it in a server and when a person click it, it will delete their account?
wtf you deserve way more likes on this
Nice video thanks for the amazing content
You saved me. Thank you so much
I have a question pwn ... I already have the knowledge on IDOR, CSRF vulnerabilities but I need to practice .. like chess ... I am happy there are softwares I can practice on relating to chess ... because I can test out ..reaarange..apply...try out anything I have learnt ... so saying that ..
are there any websites or softwares I can buy that has like 100's of IDOR vulnerabilities that I can use Burp on and practice all night?? Thanks.
this is the best. freaking cool
Come on more video , u r just awesome !!!
What about this: the malicious site has an that sends a GET request, gets the token, then sends it back and deletes the account?
Yes! We cannot access external website within but what about window.postMessage() ?
Best explanation
sorry im still not clear even after rewatching the video.
how cat.com knows what we were browsign before so they can abuse the cookies system in our browser ? do they also accessing our history browser ?
if I opening in incognito/private, can cat.com still abuse this method
Can cors prevent this request when credentials are included and the cookie is http only?
Fucking A . i had to do couple of days of deep research to understand some of those concepts in order to have some idea about where the exploits would be . you just explained it PERFECTLY in simple terms and visuals and confirmed some of my thoughts :D . u did share some valuable and accurate information despite supid youtube terms n policies. Thank you sir for the clues XD
nice video! thanks a lot!!!
Is it true that SOP allows to send request cross domain but not read the responses? Why would even a request be even triggered by the browser if there is a SOP?
most of the cases of being bypassed by other domains for a kind of request is by using */wildcard in CORS
Ok, good stuff. Subscribed.
Great video, can you please shed a bit more light on how a csrf token actually protect against a csrf attack?
Awesome Video
Your videos are amazing. Clean, informational, and perfect. I should have found your channel earlier.
But how is it possible to post json via html form, where entry is urlencoded?
I found a CSRF on a large website with > 500k members, so it's more common than you think! It allowed me to send their coins to my account, and those coins were bought with real money, so it was a decently critical flaw
Awesome as always
++ Could you please tell the shell you're using in the end?
@@tekken-pakistan2718 Sorry for the super late reply, it's Terminus - eugeny.github.io/terminus/
@@PwnFunction thanks
Welp, sorry to ask xD but you can you tell the theme too? Also, theme of visual studio, also theme of your own distro, would love to see the rice.
Nice man!
Thanks alot
I get this as response headers but I still get the chrome cross origin error.
access-control-allow-headers: Content-Type
access-control-allow-origin: localhost
content-length: 0
content-type: text/html; charset=UTF-8
date: Mon, 16 Mar 2020 15:52:28 GMT
server: Apache
status: 200
12:47
I dont understand why the json data + the content type header are first passed through a redirect(?) then to the vulnerable site?
Because simply flash will forward the request as string and then the site will convert it into header and “ key = value “ type so that it would be readable by the API of vuln.com!
Ooooooh new video!
Before sending the delete request, isn't the browser sending a preflight OPTIONS request to the server which will return an error and the delete request won't happen anymore ?
I was thinking the same. Ideally CORS would have stopped this.
yes. In case of Ajax request , SOP will stop the request as the preflight will return error
yeah. Just as a note, It seems that you can actually send a simple request to the server and the request will go through but you won't be able to read the response due to cors. namely if you don't have any headers on your request but then again that means you won't have any cookies and won't be carrying any state so pretty useless all in all.
As cors is just client sided, for a hacker this isn't difficult to bypass it
@Orora Brian You can still do CSRF for non-authenticated requests, such as an anonymous message on a blog post or something, which is not entirely harmless