Passwords & hash functions (Simply Explained)
Vložit
- čas přidán 29. 08. 2024
- How can companies store passwords safely and keep them away from hackers? Well let's find out!
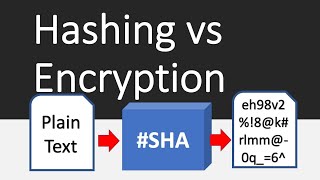
With all the data breaches lately, it's likely that the password of one of your accounts has been compromised. Hackers now might know the password you've used, but they also might not.. To understand why, we'll take a look at what methods a company can use to protect user passwords. We'll take a look at encryption, hash functions and a multilayer approach!
📚 Sources
Can be found on my website:
savjee.be/vide...
🌍 Social
Twitter: / savjee
Facebook: / savjee
Blog: savjee.be
💌 Newsletter: newsletter.savj... (no more than once a month)
❤️ Become a Simply Explained member: / @simplyexplained








We were just shown this as a part of an information systems security lecture, I figured I'd actually go ahead and give it a like because it's simple and informative
Thanks! Really appreciate that!
Brilliant video.. I love how you explain such complex concepts in a simple manner.. Please keep up the good work
good mornin sir!
Keep up the good work mate, it was informative.
Learned a great deal of things thanks to this video. Thank you.
AMAZING. really appreciated you goign through drop Box's encryption method.
started coding 8-9 months ago, doing JS now and just started learning how to use the scrypt function as well as salting passwords etc... watching this video made me excited for all the deeper things you can do... maybe one day i shall make it a goal to recreate and code that level of password security like dropbox has! cool vid. thanks again
anyone wanna share their experience with coding thus far? anyone think im doin ok learning this stuff after 8 months? or am i behind.... lol... sometimes i can't tell tbh
i still love learning all this stuff regardless lol
Thank you, Sir! It did helped me a lot in learning how hash functions actually work! And also Thank You for simplifying the concept!
Good job. Studying for Security+ exam here and the cryptography has been one thing I've found it hard to get into. It helps to have different explanations of it.
Agree. Getting ready to take mine. The more I read the more confusing it is for me. But this video just explained it all. I am no. Longer confused.
Cyber Security Dev: So which password protection do you want to use?
Dropbox: y e s
the channel name is perfect
thanks dude. 💖
Awesome video, very friendly and pleasant to watch! about dropbox- if they're not saving the keys in their db's, where do they save them? physical devices maybe?
Wow, I can't believe how well you explained that! Thank you sir!
You really explain things simply ✌️
Excellent video but I am not understanding something:
You use salt to generate a unique hash from a password (string).
When a user re-logins and you want to see the hash of his password you would also have to RE-ADD that same "unique salt" that was given when the user created the account. How do you know that "unique salt" if it was randomly generated?
Same I don't understand this
You store the hashed password with the salt
When you login, it checks if your login user/email exists in the db, if yes, then it adds the salt to the password you typed, then hash the combination and check with the hash
@@Maxxxxxxxxxxxxxxxxxxxxxxxxxxxx What if I get access to the salt you used to store the password? Isn't that a single point of failure?
@@walterlol yes but for that to happen, they would've already got access to your database.
I probably forgot to mention that the salt is usually 32byte or 64byte
Awesome video - very easy to understand and succinct, it flowed well too - very helpful thank you!
Very nice descreption. Loved it. Thank you very much ❤❤❤
clear and easy to understand this is perfect
amazing video. learnt a lot, going to share :-)
This is awesome man, thanks for explaining.
This video was incredible, thank u so much
Thank you very much for this video! Certainly learnt a lot from this and would be learning more about it in detail :)
This is the first video I saw of you!
Great as always! Please keep sharing such a good stuff!
thank you very much for the instructional - learned a lot (specially w/the salt & cost things). Nice !!! Furthermore, your voice is very pleasant so double congrats!
Great job. I love every single one of your videos!
Very informative one.. Liked it.. Well explained!! 💯
They should make a hash system that resets every hour
How would you check input password with the one you entered on registration? 😊
Excellent and clear explanation.
very informative . best explanation .
keep it up!!!
Very interesting video ! Thank you for all this nice work.
Very clear explanation , well done
Glad you liked it!
thank you so much for this vid it is very informative
Are you a hacking student?
Savjee next video should be about delegated proof of stake
Reallly informative! Thanks!
Explained very simply thank you
awesome video! Thank you!
I use a extremely long custom hashing method for my server that uses many variables indented to that user only
Nice video!
I have a question: what about saving each password with its encrypted version, using the password itself as encryption key?
This way each stored password would have a unique encryption key, instead of a single AES key shared among all the saved passwords.
But how would you store the key? That kinda just adds an unnecessary step without gaining anything
My encryption/decryption algorithms I have (for PHP) take in a string, add some salt, some hashing and then locks it with a key then encrypts or decrypts that with a very “quarantined” password that’s been... Treated. It’s strong asf.
Could u tell me how encryption works?
nice video and very well explalined - thanks a lot!!!! :)😁👍✌️
Wow so interesting. Really enjoyed this vid
Amazing video, thank you so much mate!
You mentioned something about encryption key being kept separately, how can it be queried to work on the web application? Kindly put more light
It's very nice video.. thanks for your efforts and keep it going
Excellent explanation
Wow. perfect video!!
this video is underrated
Simple and explains a lot thank you :)
Excellent work
Thank you sir Nice explain !!! thumb up
Change the unique hash stored on the database for the same password the user uses, every time the user signs in?
so regardless of the fact that each of these different methods can be breached, best course of action is to have two forms of logging in to your account a text message to your phone that you have to input when logging in to an account.
Very well explained, thanks
Well, it was really helpful video
Great video!
Best explanation
Well explained!
Why don't companies put a limit on number of login trials a computer can have? For example, can't they just reject the user for a limited period of time if they enter totally wrong credentials?
Sure they can! But in this video I'm talking about a scenario in which an attacker has managed to breach the database and has all the (hashed) passwords in his possession.
Ahh , that is not what he is talking about. If somebody stole the database of passwords. That is what he is referring to.
For example a keypass file. Is a store of encrypted passwords. If somebody stole my drive and got them. They can pound on it forever. Eventually I will be long dead and turned to dust. The reason 'Dropbox' does all this is not just for a website long in. It is in case somebody steals the hashed and encrypted storage.
You still have a lack of understanding about how this works. As far as the end user logging into a website.
Great video - thank you
thank you, very clear!
very good video , I learned the concepts in a very good way... can you kindly do a simple javascript project to make the 3 kind of protection (hashing + bcrypt + encryption) to show us how to do it practically as well
If there are numerous layers of protection around the passwords then how can the system check whether the password you've entered is correct?
In the Dropbox example, its Encryption => bcrypt => Hash => Password. Essentially, they work backwards.
First, they receive your password in plaintext which you enter into whatever login screen. Then, they hash it, and then use bcrypt on it. They will then retrieve the stored password hash from their databases, and decrypt it. At this point, the password you sent to them has been hashed, and bcrypted, and the password they stored has been decrypted, so if they are the same password, it should be equal. If they are equal, then that means you entered the correct password.
Ohhh thank you
Is hashing possible for other things like live facial recognition or fingerprints?
Excellent video and explaining the technology. However, I have a situation where I don't know how I would adapt the concepts you explained because the scenario is slightly different. Your example works interactively by comparing user passwords with stored hash values. My scenario is for an automated process (no user interaction at all) and the credentials are self-contained in the program package. These must not be known to the user or anyone who can get a hold of the file(s) containing them.
Here is a live example … We have a company application that requires administrative rights to execute but our users only have standard Windows user permissions. I repackaged the application into a single EXE executable script to conceal the admin credentials that are included in the script code. However, I discovered that compiling the script is not enough because the EXE file can be decompiled or someone can use other programs to see the contents.
How can I adapt the concepts you explained in your video this my scenario? I need to be able to execute a self-contained application package locally (no network or internet resources) and with specific credentials while protecting said credentials from the local user or anyone who might get a hold of the EXE file containing the credentials. The application needs to use these credentials at run time to perform its tasks.
Your insight is most appreciated.
Great video! thanks
very well explained
Not only to maintain unique hashes...salting also provides extra security for example you can either append or prepend salt data..that requires lot of effort from hacker to figure out
Thank you
Keep up the great work..!
I definitely will! Thank you.
wow......thank you so much...keep it up plzzz
Nice work. Thanks for helping to clear this up.
Very educative video :)
When you put up that list of the top 10 passwords, I was like, “been there, done that” 😂. These days I let my Apple devices generate and store codes for me
Nice video man.
Excellent content
thank u man it helped a lot ...!
Man, great job there. How do you do it? I would love to the the animations in portuguese. I feel it's missing here in Brazil the way you explain.
@@simplyexplained4601 You are a scammer! What a dirty technic to use the channel name and icon to do your black business.
great video
So you hash your plain text password using 'salt' and 'cost'. This means every password that's the same plain text is different.
But when comparing the password that you use to login, should you use the exact same salt and cost to hash that same plain text password?
This means you should keep the salt and hash (and cost if it isn't a constant) for every user.
Am I correct in this? This isn't explained in the video sadly.
How secure is smashing the keyboard at random while alternating the shift key?
Good work.
thank you so much.
Where/how do you store the salt and cost do you can use it when the user tries to log in?
You can store the salt in your database with the hashed password. And if you're using bcrypt, the hash, salt and cost are all in 1 string.
Simply Explained - Savjee Thanks. If I store the salt in the database (the same one that a hacker just got access to) how is that secure?
It just ensures that each hash is unique and that cracking attempts can't be speeded up with tricks like rainbow tables.
Just like the channel's name, Simply Explained!
So awesome!
[Hash + salt] Question:
How can you compare passwords if the hash alters when entering the same password?
ex.
Bob and Vagene have the same passwords "sendNudes". Both will have different hash. Bob logs in. How would you compare Bob's inputted password to the one in storage?
This has been eating at me! I NEED ANSWERS!!! pls
Awesome, thank you :)
nice!
If hash functions are one-way? Does that mean that they are many-to-one functions? If that's so, it's possible to enter your account with a totally different password with the same calculated hash?
@XOP Systems I see... Totally irreversible security sounds too good to be true
How do they compare the hashes if there is random salt?
Salt is stored seperately alongside the password..
On 4:38 you said to use different salt but I can't see it happening. If I use different salt, when I have to check the password, I would not know the used hash. If I keep it on the database, I would have the same problem as leaking the password. What I'm missing?
brilliant
The Imgur incident is misrepresented in this video. They did not store the passwords in plaintext, the hashes were solved and leaked.
keep up the good work :D
NICE VIDEO
Thanks a lot for the succinct adumbration. And by the way.
04:11 ROFL 😂
Thanks 👌👀
thank you 😍
thanks agfain...
on 'TamaTown Rewrtten' ii do sha512 then xor the resulting hash with some random bytes then sha512 it again
the original game however stored them in plaintext as there reset pass thing expects to just.. get the password back
i was wondering how to make a vivid video like this, what kind of software tool
and how i know my hash code??